在广域网技术中,BGP MPLS VPN 可以在一台路由器上通过 VPN 实例达到隔离同一台路由器上连接的相同网段的效果。其实 VPN 实例这种技术不一定非要在 BGP MPLS VPN 中使用,我们也可以把 VPN 实例的技术使用在隔离业务当中。
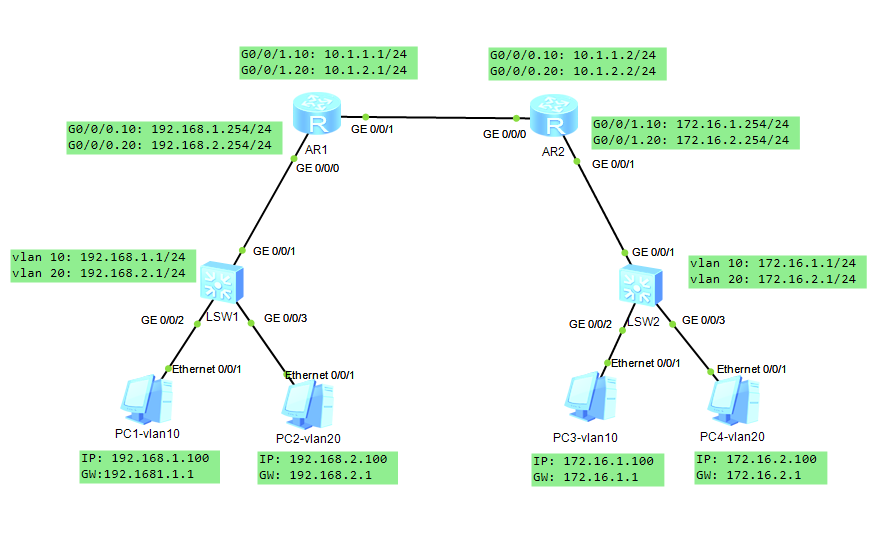
# 实验网络拓扑图
SW1 上有 vlan 10 的三层业务段和 vlan 20 的三层业务段,同样 SW2 上也有 vlan10 和 vlan20 的三层业务段。现在需要实现 SW1 上的 vlan 10 和 SW2 上的 vlan10 互通,SW1 和 SW2 上的 vlan20 互通,但是 vlan10 和 vlan20 之间两两不能互通。此时就可以使用创建多个 VPN 实例达到业务隔离的效果。
![实验网络拓扑图]()
# 实验组网
根据上述拓扑结构,配置 VPN 实现业务隔离的思路如下:
1、创建 VPN 实例
2、交换机:创建 vlan,将 vlanif 绑定 VPN 实例,接口加入对应 vlan
路由器:创建虚接口,将三层虚接口绑定 VPN 实例
3、配置 ospf 多进程
# SW1 配置
# 创建 vpn 实例
| <Huawei>system-view |
| [Huawei] sysname SW1 |
| [SW1] ip vpn-instance vpn1 // 创建 VPN 实例 |
| [SW1-vpn-instance-vpn1] ipv4-family |
| [SW1-vpn-instance-vpn1-af-ipv4] route-distinguisher 100:1 // 设置 RD |
| [SW1-vpn-instance-vpn1-af-ipv4] vpn-target 100:1 |
| [SW1-vpn-instance-vpn1-af-ipv4] q |
| [SW1-vpn-instance-vpn1] q |
| [SW1] ip vpn-instance vpn2 |
| [SW1-vpn-instance-vpn2] ipv4-family |
| [SW1-vpn-instance-vpn2-af-ipv4] route-distinguisher 200:1 |
| [SW1-vpn-instance-vpn2-af-ipv4] vpn-target 200:1 |
| [SW1-vpn-instance-vpn2-af-ipv4] q |
| [SW1-vpn-instance-vpn2] q |
# 创建 vlan,将 vlanif 绑定 VPN 实例
| [SW1] vlan batch 10 20 |
| [SW1] interface Vlanif 10 |
| [SW1-Vlanif10] ip binding vpn-instance vpn1 // 把三层虚接口绑定 VPN 实例 |
| [SW1-Vlanif10] ip address 192.168.1.1 24 |
| [SW1-Vlanif10] q |
| [SW1] int Vlanif 20 |
| [SW1-Vlanif20] ip binding vpn-instance vpn2 |
| [SW1-Vlanif20] ip address 192.168.2.1 24 |
# 交换机接口加入对应 vlan
此处将 G0/0/1 设置为 trunk,G0/0/2 和 G0/0/3 分别采用 access 和 hybrid,在 F&Q 中将解释这两种接口的区别
| [SW1] int GigabitEthernet 0/0/1 |
| [SW1-GigabitEthernet0/0/1] port link-type trunk |
| [SW1-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 20 |
| [SW1-GigabitEthernet0/0/1] q |
| [SW1] int GigabitEthernet 0/0/2 |
| [SW1-GigabitEthernet0/0/2] port link-type access |
| [SW1-GigabitEthernet0/0/2] port default vlan 10 |
| [SW1-GigabitEthernet0/0/2] q |
| [SW1] interface GigabitEthernet 0/0/3 |
| [SW1-GigabitEthernet0/0/3] port link-type hybrid |
| [SW1-GigabitEthernet0/0/3] port hybrid untagged vlan 20 |
| [SW1-GigabitEthernet0/0/3] port hybrid pvid vlan 20 |
| [SW1-GigabitEthernet0/0/3] q |
# 配置 OSPF 多进程
创建基于实例的 ospf,这样可以把 vlan10 和 vlan20 的路由进行分别学习,从而到达业务隔离的效果
| [SW1] ospf 1 vpn-instance vpn1 |
| [SW1-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255 |
| [SW1-ospf-1-area-0.0.0.0] q |
| [SW1-ospf-1] q |
| [SW1] ospf 2 vpn-instance vpn2 |
| [SW1-ospf-2] area 0.0.0.0 |
| [SW1-ospf-2-area-0.0.0.0] network 192.168.2.0 0.0.0.255 |
# R1 配置
# 创建 vpn 实例
| <Huawei>system-view |
| [Huawei] sysname R1 |
| [R1] ip vpn-instance vpn1 |
| [R1-vpn-instance-vpn1] ipv4-family |
| [R1-vpn-instance-vpn1-af-ipv4] route-distinguisher 100:1 |
| [R1-vpn-instance-vpn1-af-ipv4] vpn-target 100:1 |
| [R1-vpn-instance-vpn1-af-ipv4] q |
| [R1-vpn-instance-vpn1] q |
| [R1] ip vpn-instance vpn2 |
| [R1-vpn-instance-vpn2] ipv4-family |
| [R1-vpn-instance-vpn2-af-ipv4] route-distinguisher 200:1 |
| [R1-vpn-instance-vpn2-af-ipv4] vpn-target 200:1 |
| [R1-vpn-instance-vpn2-af-ipv4] q |
| [R1-vpn-instance-vpn2] q |
# 创建虚接口,将三层虚接口绑定 VPN 实例
| [R1] int GigabitEthernet 0/0/0.10 |
| [R1-GigabitEthernet0/0/0.10] ip binding vpn-instance vpn1 |
| [R1-GigabitEthernet0/0/0.10] ip address 192.168.1.254 24 |
| [R1-GigabitEthernet0/0/0.10] dot1q termination vid 10 // 路由器的子接口要生效,需要给子接口强制打上 vlan10 或者 vlan20 的标记 |
| [R1-GigabitEthernet0/0/0.10] arp broadcast enable // 开启子接口 arp 广播 |
| [R1-GigabitEthernet0/0/0.10] q |
| [R1] int GigabitEthernet 0/0/0.20 |
| [R1-GigabitEthernet0/0/0.20] ip binding vpn-instance vpn2 |
| [R1-GigabitEthernet0/0/0.20] ip address 192.168.2.254 24 |
| [R1-GigabitEthernet0/0/0.20] dot1q termination vid 20 |
| [R1-GigabitEthernet0/0/0.20] arp broadcast enable |
| [R1-GigabitEthernet0/0/0.20] q |
| [R1] int GigabitEthernet 0/0/1.10 |
| [R1-GigabitEthernet0/0/1.10] ip binding vpn-instance vpn1 |
| [R1-GigabitEthernet0/0/1.10] ip address 10.1.1.1 24 |
| [R1-GigabitEthernet0/0/1.10] dot1q termination vid 10 |
| [R1-GigabitEthernet0/0/1.10] arp broadcast enable |
| [R1-GigabitEthernet0/0/1.10] q |
| [R1] int GigabitEthernet 0/0/1.20 |
| [R1-GigabitEthernet0/0/1.20] ip binding vpn-instance vpn2 |
| [R1-GigabitEthernet0/0/1.20] ip address 10.1.2.1 24 |
| [R1-GigabitEthernet0/0/1.20] dot1q termination vid 20 |
| [R1-GigabitEthernet0/0/1.20] arp broadcast enable |
# 配置 OSPF 多进程
| [R1] ospf 1 vpn-instance vpn1 |
| [R1-ospf-1] area 0.0.0.0 |
| [R1-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255 |
| [R1-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255 |
| [R1-ospf-1-area-0.0.0.0] q |
| [R1-ospf-1] q |
| [R1] ospf 2 vpn-instance vpn2 |
| [R1-ospf-2] area 0.0.0.0 |
| [R1-ospf-2-area-0.0.0.0] network 192.168.2.0 0.0.0.255 |
| [R1-ospf-2-area-0.0.0.0] network 10.1.2.0 0.0.0.255 |
# R2 配置
# 创建 vpn 实例
| <Huawei>system-view |
| [Huawei] sysname R2 |
| [R2] ip vpn-instance vpn1 |
| [R2-vpn-instance-vpn1] ipv4-family |
| [R2-vpn-instance-vpn1-af-ipv4] route-distinguisher 100:1 |
| [R2-vpn-instance-vpn1-af-ipv4] vpn-target 100:1 |
| [R2-vpn-instance-vpn1-af-ipv4] q |
| [R2-vpn-instance-vpn1] q |
| [R2] ip vpn-instance vpn2 |
| [R2-vpn-instance-vpn2] ipv4-family |
| [R2-vpn-instance-vpn2-af-ipv4] route-distinguisher 200:1 |
| [R2-vpn-instance-vpn2-af-ipv4] vpn-target 200:1 |
| [R2-vpn-instance-vpn2-af-ipv4] q |
| [R2-vpn-instance-vpn2] q |
# 创建虚接口,将三层虚接口绑定 VPN 实例
| [R2] int g0/0/0.10 |
| [R2-GigabitEthernet0/0/0.10] ip binding vpn-instance vpn1 |
| [R2-GigabitEthernet0/0/0.10] ip address 10.1.1.2 24 |
| [R2-GigabitEthernet0/0/0.10] dot1q termination vid 10 |
| [R2-GigabitEthernet0/0/0.10] arp broadcast enable |
| [R2-GigabitEthernet0/0/0.10] q |
| [R2] int g0/0/0.20 |
| [R2-GigabitEthernet0/0/0.20] ip binding vpn-instance vpn2 |
| [R2-GigabitEthernet0/0/0.20] ip address 10.1.2.2 24 |
| [R2-GigabitEthernet0/0/0.20] dot1q termination vid 20 |
| [R2-GigabitEthernet0/0/0.20] arp broadcast enable |
| [R2-GigabitEthernet0/0/0.20] q |
| [R2] int GigabitEthernet 0/0/1.10 |
| [R2-GigabitEthernet0/0/1.10] ip binding vpn-instance vpn1 |
| [R2-GigabitEthernet0/0/1.10] ip address 172.16.1.254 24 |
| [R2-GigabitEthernet0/0/1.10] dot1q termination vid 10 |
| [R2-GigabitEthernet0/0/1.10] arp broadcast enable |
| [R2-GigabitEthernet0/0/1.10] q |
| [R2] int GigabitEthernet 0/0/1.20 |
| [R2-GigabitEthernet0/0/1.20] ip binding vpn-instance vpn2 |
| [R2-GigabitEthernet0/0/1.20] ip address 172.16.2.254 24 |
| [R2-GigabitEthernet0/0/1.20] dot1q termination vid 20 |
| [R2-GigabitEthernet0/0/1.20] arp broadcast enable |
# 配置 OSPF 多进程
| [R2] ospf 1 vpn-instance vpn1 |
| [R2-ospf-1] area 0.0.0.0 |
| [R2-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255 |
| [R2-ospf-1-area-0.0.0.0] network 172.16.1.0 0.0.0.255 |
| [R2-ospf-1-area-0.0.0.0] q |
| [R2-ospf-1] q |
| [R2] ospf 2 vpn-instance vpn2 |
| [R2-ospf-2] area 0.0.0.0 |
| [R2-ospf-2-area-0.0.0.0] network 10.1.2.0 0.0.0.255 |
| [R2-ospf-2-area-0.0.0.0] network 172.16.2.0 0.0.0.255 |
# SW2 配置
# 创建 vpn 实例
| <Huawei>system-view |
| [Huawei] sysname SW2 |
| [SW2] ip vpn-instance vpn1 |
| [SW2-vpn-instance-vpn1] ipv4-family |
| [SW2-vpn-instance-vpn1-af-ipv4] route-distinguisher 100:1 |
| [SW2-vpn-instance-vpn1-af-ipv4] vpn-target 100:1 |
| [SW2-vpn-instance-vpn1-af-ipv4] q |
| [SW2-vpn-instance-vpn1] q |
| [SW2] IP vpn-instance vpn2 |
| [SW2-vpn-instance-vpn2] ipv4-family |
| [SW2-vpn-instance-vpn2-af-ipv4] route-distinguisher 200:1 |
| [SW2-vpn-instance-vpn2-af-ipv4] vpn-target 200:1 |
| [SW2-vpn-instance-vpn2-af-ipv4] q |
| [SW2-vpn-instance-vpn2] q |
| [SW2] |
# 创建 vlan,将 vlanif 绑定 VPN 实例
| [SW2] vlan batch 10 20 |
| [SW2] int Vlanif 10 |
| [SW2-Vlanif10] ip binding vpn-instance vpn1 |
| [SW2-Vlanif10] ip address 172.16.1.1 24 |
| [SW2-Vlanif10] q |
| [SW2] int Vlanif 20 |
| [SW2-Vlanif20] ip binding vpn-instance vpn2 |
| [SW2-Vlanif20] ip address 172.16.2.1 24 |
# 交换机接口加入对应 vlan
| [SW2] int GigabitEthernet 0/0/1 |
| [SW2-GigabitEthernet0/0/1] port link-type trunk |
| [SW2-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 20 |
| [SW2-GigabitEthernet0/0/1] q |
| [SW2] int g0/0/2 |
| [SW2-GigabitEthernet0/0/2] port link-type access |
| [SW2-GigabitEthernet0/0/2] port default vlan 10 |
| [SW2-GigabitEthernet0/0/2] q |
| [SW2] interface GigabitEthernet 0/0/3 |
| [SW2-GigabitEthernet0/0/3] port link-type hybrid |
| [SW2-GigabitEthernet0/0/3] port hybrid untagged vlan 20 |
| [SW2-GigabitEthernet0/0/3] port hybrid pvid vlan 20 |
# 配置 OSPF 多进程
| [SW2] ospf 1 vpn-instance vpn1 |
| [SW2-ospf-1] area 0.0.0.0 |
| [SW2-ospf-1-area-0.0.0.0] network 172.16.1.0 0.0.0.255 |
| [SW2-ospf-1-area-0.0.0.0] q |
| [SW2-ospf-1] q |
| [SW2] ospf 2 vpn-instance vpn2 |
| [SW2-ospf-2] area 0.0.0.0 |
| [SW2-ospf-2-area-0.0.0.0] network 172.16.2.0 0.0.0.255 |
# 实验验证
配置完成后,SW1 和 SW2 上相同的 vlan 可以互通,不同 vlan 之间不能互通
使用 PC1 ping PC3 可以通信,PC1 ping PC4 无法通信
使用 AR1 ping AR2 的 G0/0/1.10 能够通信,ping G0/0/1.20 无法通信
| [R1] ping -vpn-instance vpn1 -a 192.168.1.254 172.16.1.254 |
| PING 172.16.1.254: 56 data bytes, press CTRL_C to break |
| Reply from 172.16.1.254: bytes=56 Sequence=1 ttl=255 time=20 ms |
| Reply from 172.16.1.254: bytes=56 Sequence=2 ttl=255 time=30 ms |
| Reply from 172.16.1.254: bytes=56 Sequence=3 ttl=255 time=10 ms |
| Reply from 172.16.1.254: bytes=56 Sequence=4 ttl=255 time=10 ms |
| Reply from 172.16.1.254: bytes=56 Sequence=5 ttl=255 time=30 ms |
| |
| --- 172.16.1.254 ping statistics --- |
| 5 packet (s) transmitted |
| 5 packet (s) received |
| 0.00% packet loss |
| round-trip min/avg/max = 10/20/30 ms |
| |
| [R1] ping -vpn-instance vpn1 -a 192.168.1.254 172.16.2.254 |
| PING 172.16.2.254: 56 data bytes, press CTRL_C to break |
| Request time out |
| Request time out |
| Request time out |
| Request time out |
| Request time out |
| |
| --- 172.16.2.254 ping statistics --- |
| 5 packet (s) transmitted |
| 0 packet (s) received |
| 100.00% packet loss |
查看 vpn 实例的路由,发现 SW1 上 vpn 只学到相同 vpn 的路由
| [SW1] display ip routing-table vpn-instance vpn1 |
| Route Flags: R - relay, D - download to fib |
| ------------------------------------------------------------------------------ |
| Routing Tables: vpn1 |
| Destinations : 4 Routes : 4 |
| |
| Destination/Mask Proto Pre Cost Flags NextHop Interface |
| |
| 10.1.1.0/24 OSPF 10 2 D 192.168.1.254 Vlanif10 |
| 172.16.1.0/24 OSPF 10 3 D 192.168.1.254 Vlanif10 |
| 192.168.1.0/24 Direct 0 0 D 192.168.1.1 Vlanif10 |
| 192.168.1.1/32 Direct 0 0 D 127.0.0.1 Vlanif10 |
| |
| [SW1] display ip routing-table vpn-instance vpn2 |
| Route Flags: R - relay, D - download to fib |
| ------------------------------------------------------------------------------ |
| Routing Tables: vpn2 |
| Destinations : 4 Routes : 4 |
| |
| Destination/Mask Proto Pre Cost Flags NextHop Interface |
| |
| 10.1.2.0/24 OSPF 10 2 D 192.168.2.254 Vlanif20 |
| 172.16.2.0/24 OSPF 10 3 D 192.168.2.254 Vlanif20 |
| 192.168.2.0/24 Direct 0 0 D 192.168.2.1 Vlanif20 |
| 192.168.2.1/32 Direct 0 0 D 127.0.0.1 Vlanif20 |
# F & Q
# 一、在交换机的接口配置中,hybrid 口和 access 口有什么区别?
在华为交换机中,接口的端口类型(access、hybrid、trunk)决定了该端口如何处理 VLAN 标签。下面是每种端口类型的基本解释:
Access 端口:通常用于连接终端设备,如 PC。Access 端口只能属于一个 VLAN,并且发送和接收的帧都是未打标签的(untagged)。当数据帧通过 Access 端口时,交换机会将 VLAN 标签添加到帧中(发送时)或移除 VLAN 标签(接收时)。
Hybrid 端口:可以属于多个 VLAN,并且可以发送和接收打标签的(tagged)和未打标签的(untagged)帧。Hybrid 端口允许配置一个默认的 VLAN(PVID),该 VLAN 的帧将以未打标签的形式发送。
Trunk 端口:通常用于交换机之间的连接。Trunk 端口可以属于多个 VLAN,并且发送和接收的帧都是打标签的(tagged),除非配置了特定的 VLAN 以未打标签的形式发送。
在上述 SW 的配置中,如果使用 access,则仅需配置 port default vlan 10 ,接口会将 VLAN 10 设置为默认 VLAN。PC 发送的帧是未打标签的,交换机会将这些帧视为属于 VLAN 10。
如果使用 hybrid, port hybrid tagged vlan 10 表示将 VLAN 10 配置为打标签的 VLAN。这意味着交换机期望接收到的 VLAN 10 的帧是带有 VLAN 标签的。然而,PC 通常不会发送带有 VLAN 标签的帧,因此交换机无法正确处理这些帧,这会导致通信失败。
为了解决这个问题,在 Hybrid 端口配置中为 VLAN 10 设置一个未打标签的默认 VLAN(PVID),这样 PC 发送的未打标签帧就会被交换机视为属于 VLAN 10。配置如下:
| [SW1] interface GigabitEthernet 0/0/1 |
| [SW1-GigabitEthernet0/0/1] port link-type hybrid |
| [SW1-GigabitEthernet0/0/1] port hybrid untagged vlan 10 // 此处将 tagged 改为 untagged |
| [SW1-GigabitEthernet0/0/1] port hybrid pvid vlan 10 |
| [SW1-GigabitEthernet0/0/1] quit |
# 二、为什么在绑定 vpn 后接口 IP 消失了?
在华为设备的配置中,当你为一个接口配置 VPN 实例时,该接口上原有的 IPv4 和 IPv6 配置会被清除。这是因为在 VPN 实例中,接口的 IP 地址配置将与 VPN 实例相关联,而不是直接与物理接口相关联。
所以配置 IP 的操作应该在绑定 vpn 之后
| [R1-GigabitEthernet0/0/0.10] ip address 192.168.1.254 24 |
| [R1-GigabitEthernet0/0/0.10] ip binding vpn-instance vpn1 |
| Info: All IPv4 related configurations on this interface are removed! |
| Info: All IPv6 related configurations on this interface are removed! |
# 三、为什么在 SW1 上 ping 不通 AR2 ?
现象为:在 SW1 上 ping 不通 AR2 ,在 AR1 上能 ping 通 SW1 和 AR2,抓包后显示,ping 命令从 AR1 的 G0/0/0.10 进入,未能从 G0/0/1.10 发出。
在路由器的子接口配置中,有两个重要的配置命令:
| [R1] int g0/0/0.10 // 进入子接口 |
| [R1-GigabitEthernet0/0/0.10] ip add 192.168.1.254 24 /// 配置子接口地址 |
| [R1-GigabitEthernet0/0/0.10] dot1q termination vid 10 // 标记终止的 vid 编号 |
| [R1-GigabitEthernet0/0/0.10] arp broadcast enable // 开启子接口的 arp 广播(默认不开启) |
dot1q termination vid 10 路由器的子接口要生效,需要给子接口强制打上 vlan10 或者 vlan20 的标记
arp broadcast enable 需要开启子接口的 arp 广播,可通过 display arp vpn-instance vpn1 自行验证开关 arp 广播后 arp 表的差异。